Page Contents :
In the next few posts, we will further explore some basic knowledge and technologies of blockchain:
- Cryptography and hash functions
- What is a block and how it forms a chain
- The role of nodes
- How the blockchain network works
What Is Cryptography?
What is cryptography and how does it work? Everyone appears to be aware of it, but not quite sure about it.
In real life, we often need to use a password: for example, we must input the password to withdraw money from a bank’s ATM.
On the Internet, when using some internet services, we use different ids and passwords: for example, to access our mailbox, or to perform online banking services.
- A password is a ciphertext that uses an encrypting algorithm to turn identifiable data into unidentifiable data.
- Cryptography is the technical science that studies the creation and deciphering of codes.
With the popularization of the Internet, it has become more difficult to protect personal digital assets from being stolen. As a result, cryptography is much more crucial.
The Caesar Cipher Of Ancient Greece
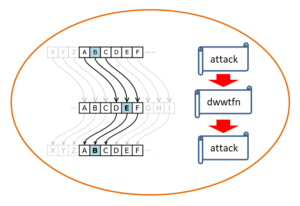
The history of cryptography can be traced back to the ancient Greek era before the Christian era. The ancient Greeks used cryptography to transmit military secret letters. As illustrated in the picture above, the ancient Greek Julius Caesar took the lead in using the “Caesar cipher”, which is to shift the letters to the next 3 positions in order, such as altering the letter A to the letter D and the letter B to the letter E. The decryption method of the ciphertext is to shift each letter forward 3 positions.
As an illustration, one day Caesar Julius bring his armies to conquer a nearby castle, and his two infantry divisions would flank the other two sides. If Caesar instructs his scout to relay orders to his two generals, then the enemy spies may be aware of their military activity. So, after encrypting his secret letter, Caesar instructed the scout to deliver a message to his two generals, instructing them to prepare food. At the same time, the scout surreptitiously handed the two generals Caesar’s secret letter. Even if enemy spies managed to obtain the secret letter, they would be unable to comprehend its contents.
The enemy’s spies only detected that Caesar’s armies were preparing to make food, and relayed the information back to his castle ruler. Following confirmation of this information, the castle ruler relaxed and allow his army to prepare meals as well. However, after Caesar’s secret letter was decrypted, his true instructions were: ATTACK.
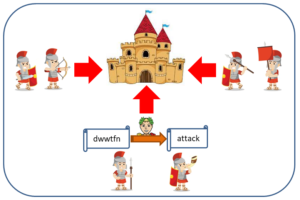
Caesar’s three major armies staged a surprise attack while the enemy army was busy preparing food. The castle ruler just realized that Caesar had duped him. What will happen in the end is very evident.
Well, it seems to be a bit of a digression! From here we can know that encrypted messages can be used to distract the opponent and perform more important functions.
So the basic function of encryption is to scramble the messages we want to sent using special algorithms. For everyone who sees the information, this is just a bunch of gibberish. The only people who can really understand the information are those who have access to the algorithm or who can figure out the algorithm.
When we first looked at Caesar’s password, we thought it was a very simple password, which could be very easy to break. But thousands of years ago, this was a fantastic invention.
How Does Public Key Cryptography Solve The Problems We Face?
Now flashback to our current Internet world, in the information transmission on the Internet, all information must be transmitted through a third-party node.
If Bod sends a message from node 1 to Alice of node 3, if there is no encryption, then all open network nodes through which the information passes, for example, at node 2, anyone can intercept the information and read Bod’s information clearly.
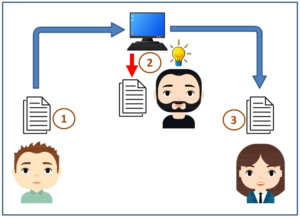
It’s as if Bod writes a note in the class and then asks John for assistance in passing the note to Alice in the front row, then John can clearly know the note’s content. If Bod has a crucial message to pass to Alice, he certainly doesn’t want John to know about it.
The issue is that the transmission of messages on our Internet is unencrypted. Is there any way to ensure that Bod’s message is only understood by Alice? There is, it’s called public key cryptography, also known as asymmetric cryptography.
In this kind of cryptography, it has a pair of keys, one is a private key and the other is a public key. If we encrypt information with a public key, we can only decrypt it with its matching private key.
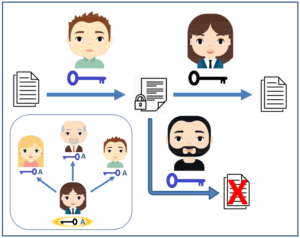
The public key can be shared with everyone in the network. For example, Alice can share her public key A with her boyfriend Bod, best friend Mary, or even her boss George. As a result, including those cyber scammers and hackers, anyone on the Internet can easily access Alice’s public key A, but they cannot guess Alice’s private key A based on public key A, nor can they use public key A to crack the information encrypted by the public key A. Therefore, Alice must keep the private key A well and not share it with others. Both the private key and the public key are very large prime numbers, and it can be said that it is impossible to reversely crack the encrypted information.
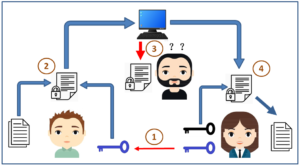
The working principle of public key cryptography is as follows:
Why We Need Public Key Cryptography In Blockchain?
What is the relationship between public key cryptography and blockchain, as we’ve discussed so much?
When you conduct cryptocurrency transactions through the blockchain, virtually all currencies are sent to the so-called hashed version of the “public key”. This public key is generated by a private key, which is a wallet import format composed of numbers and letters, and then passes through a cryptographic hash function to generate a so-called cryptocurrency wallet (WIF, Wallet Import Format) address. The generation process is irreversible.
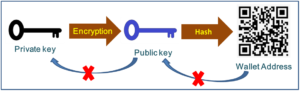
From the above example, we can clearly find that public key cryptography is an indispensable part of the blockchain security protocol. In the blockchain, It is the basis of encrypted token transactions and identity verification.
In the next post, we will further explore the hash function in public key cryptography, and understand how it is calculated and applied.





Very good post. I absolutely appreciate this website. Stick with it!